This book attempts to define an approach to industrial network security that considers the unique network, protocol, and application characteristics of an Industrial Control System (ICS), while also taking into consideration a variety of common compliance controls. For the purposes of this book, a common definition of ICS will be used in lieu of the more specific Supervisory Control and Data Acquisition (SCADA) or Distributed Control System (DCS) terms.
Note that these and many other specialized terms are used extensively throughout the book. While we have made an effort to define them all, an extensive glossary has also been included to provide a quick reference if needed. If a term is included in the glossary, it will be printed in bold type the first time that it is used.
Although many of the techniques described herein—and much of the general guidance provided by regulatory standards organizations—are built upon common enterprise security methods, references and readily available information security tools, there is little information available about how these apply to an industrial network. This book attempts to rectify this by providing deployment and configuration guidance where possible, and by identifying why security controls should be implemented, where they should be implemented, how they should be implemented, and how they should be used.
- The ebook consists of 13 chapters:
+ CHAPTER 1: Introduction
+ CHAPTER 2: ABOUT INDUSTRIAL NETWORKS
In this chapter, there is a brief primer of industrial control systems, industrial networks, critical infrastructure, common cyber security guidelines, and other terminology specific to the lexicon of industrial cyber security. The goal of this chapter is to provide a baseline of information from which topics can be explored in more detail in the following chapters (there is also an extensive Glossary included to cover the abundance of new acronyms and terms used in industrial control networks). Chapter 2 also
covers some of the basic misperceptions about industrial cyber security, in an attempt to rectify any misunderstandings prior to the more detailed discussions that will follow.
CHAPTER 3: INDUSTRIAL CYBER SECURITY, HISTORY, AND TRENDS
Chapter 3 is a primer for industrial cyber security. It introduces industrial network cyber security in terms of its history and evolution, by examining the interrelations between “general” networking, industrial networking, and potentially critical infrastructures. Chapter 3 covers the importance of securing industrial networks, discusses the impact of a successful industrial attack, and provides examples of real historical incidents—including a discussion of the Advanced Persistent Threat and
the implications of cyber war.
CHAPTER 4: INTRODUCTION TO ICS AND OPERATIONS
It is impossible to understand how to adequately secure an industrial control environment without first understanding the fundamentals of ICSs and operations. These systems use specialized devices, applications, and protocols because they perform functions that are different than enterprise networks, with different requirements, operational priorities, and security considerations. Chapter 4 discusses control system assets, operations, protocol basics, how control processes are managed, and common
systems and applications with special emphasis on smart grid operations.
CHAPTER 5: ICS NETWORK DESIGN AND ARCHITECTURE
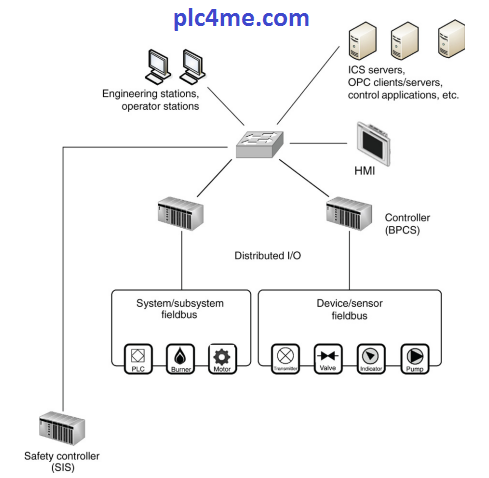
Industrial networks are built from a combination of Ethernet and IP networks (to interconnect general computing systems and servers) and at least one real-time network or fieldbus (to connect devices and process systems). These networks are typically nested deep within the enterprise architecture, offering some implied layers of protection against external threats. In recent years, the deployment of remote access and wireless networks within industrial systems have offered new entry points into
these internal networks. Chapter 5 provides an overview of some of the more common industrial network designs and architectures, the potential risk they present, and some of the methods that can be used to select appropriate technologies and strengthen these critical industrial systems.
CHAPTER 6: INDUSTRIAL NETWORK PROTOCOLS
This chapter focuses on industrial network protocols, including Modbus, DNP3, OPC, ICCP, CIP, Foundation Fieldbus HSE, Wireless HART, Profinet and Profibus, and others. This chapter will also introduce vendor-proprietary industrial protocols, and the implications they have in securing industrial networks. The basics of protocol operation, frame format, and security considerations are provided for each, with security recommendations being made where applicable. Where properly disclosed vulnerabilities or exploits are available, examples are provided to illustrate
the importance of securing industrial communications.
CHAPTER 7: HACKING INDUSTRIAL SYSTEMS
Understanding effective cyber security requires a basic understanding of the threats that exist. Chapter 7 provides a high-level overview of common attack methodologies, and how industrial networks present a unique attack surface with common attack vectors to many critical areas.
CHAPTER 8: RISK AND VULNERABILITY ASSESSMENTS
Industrial control systems are often more susceptible to a cyber-attack, yet they are also more difficult to patch due to the extreme uptime and reliability requirements of operational systems. Chapter 8 focuses on risk and vulnerability assessment strategies that specifically address the unique challenges of assessing risk in industrial networks, in order to better understand—and therefore reduce—the vulnerabilities and threats facing these real-time systems.
CHAPTER 9: ESTABLISHING ZONES AND CONDUITS
A strong cyber security strategy requires the isolation of devices into securable groups. Chapter 9 looks at how to separate functional groups and where functional boundaries should be implemented, using the Zone and Conduit model originated by the Purdue Research Foundation in 1989 and later adapted by ISA 99 (now known as ISA/IEC 62443).
CHAPTER 10: IMPLEMENTING SECURITY AND ACCESS CONTROLS
Once the industrial architecture has been appropriately divided into defined zones and the associated communication conduits between these zones, it is necessary to deploy appropriate security controls to enforce network security. Chapter 10 discusses the vital activity of network segmentation and how network- and host-based security controls are implemented.
CHAPTER 11: EXCEPTION, ANOMALY, AND THREAT DETECTION
Awareness is the prerequisite of action, according to the common definition of situational awareness. Awareness in turn requires an ability to monitor for and detect threats. In this chapter, several contributing factors to obtaining situational awareness are discussed, including how to use anomaly detection, exception reporting, and information correlation for the purposes of threat detection and risk management.
CHAPTER 12: SECURITY MONITORING OF INDUSTRIAL CONTROL
SYSTEMS
Completing the cycle of situational awareness requires further understanding and analysis of the threat indicators that you have learned how to detect in Chapter 11. Chapter 12 discusses how obtaining and analyzing broader sets of information can help you better understand what is happening, and make better decisions. This includes recommendations of what to monitor, why, and how. Information management strategies—including log and event collection, direct monitoring, and correlation using security information and event management (SIEM)—are discussed,
including guidance on data collection, retention, and management.

>>> Link Download Ebook ( MEGA.NZ Link – Easy for download )
+ Download Industrial Network Security, Second Edition – Ebook.PDF
Password Extract: plc4me.com
Thanks for reading !








